Decentralized Identity (DID) systems are a new approach to identity management that seeks to give individuals and organizations more control over their own digital identity. DID systems are based on the concept of self-sovereign identity, which means that the individual or organization is in charge of their own identity rather than relying on a centralized authority (such as a government or large corporation) to issue and manage their identity.
Benefits Of A Decentralized Identity System
There are several key benefits of a Decentralized Identity System, some of which are:
Increased Control & Privacy: In a decentralized identity system, the individual or organization is in control of its own identity and can choose what information is shared and with whom. It can help to protect privacy and prevent identity theft.
Interoperability: DID systems are designed to be interoperable, meaning that they can work with different decentralized platforms and technologies. This makes it easier for individuals and organizations to use their digital identities across various applications and services.
Decentralization: DID systems are decentralized, meaning that any organization or person does not control them. It can help prevent censorship and ensure the system is more resilient and secure.
Introducing decentralized identity systems to individuals and organizations can help offer increased control and privacy, interoperability, and decentralization. Moreover, it provides examples of how DID systems can be used in real-world scenarios, such as logging into websites or accessing medical records.
How Does A Decentralized Identity System Work?
A Decentralized Identity System includes the following main elements:
Blockchain
A Decentralized Database shared among computers in the blockchain network records information in such a way that it makes it very difficult to change, hack, or cheat the system.
Decentralized Identity Wallet
A DID is a digital wallet that manages DIDs and the private keys associated with them. It allows the owner of the DID to sign digital documents or transactions and access services or applications that require DID authentication.
To use a DID wallet, the owner of the DID will typically need to install a DID wallet application on their device. They can then use this application to create a new DID or import an existing one. Once the DID is brought into the wallet, the owner can sign transactions or access services that require DID authentication.
In addition to storing a DID and its associated private key, a DID wallet can store other cryptographic keys or credentials. It can be useful for managing access to multiple services or applications that require DID authentication.
Overall, DID wallets play a central role in the functioning of a DID system. They allow individuals and organizations to manage and use their DIDs to authenticate their identity online and provide a secure way to store and access the private key associated with a DID.
Decentralized Identifiers
Decentralized Identifiers (DIDs) are new identifiers that allow individuals and corporations to take control of their online identities. They are decentralized, meaning that any single entity, such as a government or corporation, does not control them. In contrast, distributed ledgers like Blockchains can be used to verify identity securely and transparently.
One of the key benefits of DIDs is that they allow individuals to have more control over their personal information and how it is used. For example, if you have a DID, you can choose which organizations or individuals can access your personal information and revoke access at any time. It can assist in reducing the risk of identity theft and protect your privacy.
Overall, DIDs are a promising technology that has the prospect of revolutionizing the way we assume about and manage online identity.
Decentralized Identifier (DID) Key Component
There are several key components of a Decentralized Identifier (DID):
- DID Document: It contains information about the DID, including the methods that can be used to authenticate the DID and the associated services.
- DID Method: This is a set of rules that define how a DID can be used and how it is stored on a distributed ledger.
- DID URI: It is a unique identifier that is associated with a DID and is used to look up the DID Document.
- DID Controller: This entity controls the DID and has the authority to update the DID Document.
- DID Subject: This is the entity with which the DID is associated, such as an individual or organization.
- Service Endpoint: This URL can access a service associated with the DID, such as a messaging or a payment service.
Overall, these components work together to create a decentralized system for managing identity that is secure and transparent and gives individuals and organizations more control over their personal information.
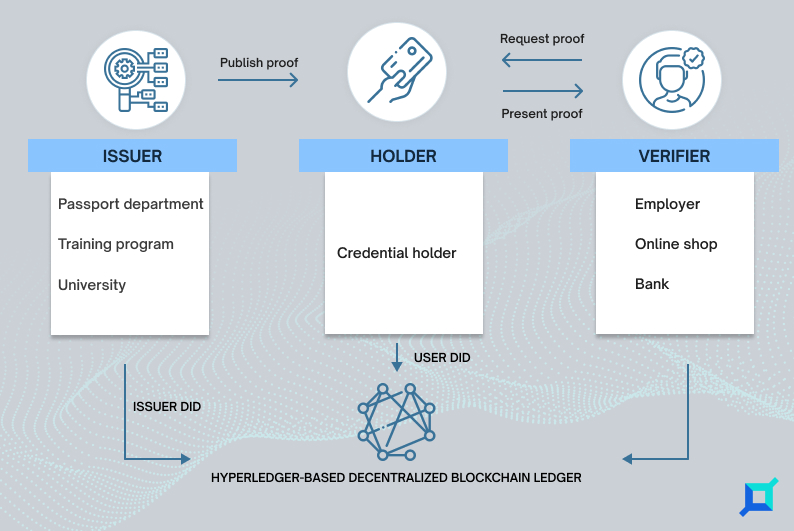
Verifiable Credential (VC)
Digital, cryptographically secured versions of the paper and digital credentials that individuals can represent to organizations needing them for verification. These are the main parties in the VC system:
- Holder: A user who receives a Verifiable Credential after creating a decentralized identifier with a digital wallet app.
- Issuer: The association signs a Verifiable Credential with their private key and issues it to the holder.
- Verifier: A party that checks the credentials and can read the issuer’s public DID on the blockchain to verify if the Verifiable Credential the holder shared was signed by the issuer’s DID.
Know How Centralized Identity System Flow Works with DID & Verifiable Credential?
Here is an example of how a centralized Identity system flow Works with DID and Verifiable credentials:
1. Issuance
A subject (e.g., an individual) requests a verifiable credential from an issuer (e.g., a government agency). The issuer verifies the claims made by the subject and issues the verifiable credential, a digital record containing the claims, and a digital signature from the issuer.
2. Storage
The subject stores the verifiable credential in a decentralized identity wallet, a secure digital repository for storing and managing decentralized identifiers and verifiable credentials. The subject’s decentralized identifier, a self-owned identifier that is unique and cryptographically verifiable, is use to identify & authenticate the wallet of the subject.
3. Presentation
The subject presents the verifiable credential to a verifier (e.g., a service provider) as proof of a specific claim (e.g., age, employment status). The verifier can verify the verifiable credential’s authenticity by checking the issuer’s digital signature and the subject’s decentralized identifier.
4. Verification
If the verifier trusts the issuer and the subject’s decentralized identifier, it can accept the verifiable credential as evidence and grant the subject access to a service or other benefit. Additionally, if the verifier does not trust the issuer or the subject’s decentralized identifier, it can request additional evidence or information from the subject.
DID Protocols and Frameworks
Several decentralized identity protocols have been developed to enable the creation and management of DIDs. Some of the most widely used DID protocols include:
World Wide Web Consortium’s (W3C) DID Specification: This is the primary standard for DIDs, and it defines a common syntax and structure for DID records, as well as a set of standard methods that can be used to create, update, and deactivate DIDs.
Hyperledger Indy: This is an open-source framework for building decentralized identity applications. It includes a set of modular components that one can use to create and manage DIDs on various blockchains.
Hyperledger Indy is a permissioned blockchain, meaning only authorized participants can access the network. Moreover, it can provide better privacy protection for identity information than public blockchains, where data is visible to anyone.
Veramo: It is a JavaScript (JS) framework that makes it easy for anyone to employ cryptographically verifiable data in their applications. Developers can use DIDs, verifiable credentials, and data-centric protocols to provide next-generation features to their users.
Overall, DID protocols provide a set of rules and standards that are used to create, manage, and use DIDs in a decentralized manner.
Wrapping Up
With decentralized identity technology, many problems caused by centralized and federated identity management systems can be solved, including certificate fraud, slow and expensive verification processes, and data breaches.
Moreover, you can connect with a reliable Blockchain company like Infrablok to get tools and infrastructure for creating DIDs on the permissioned and permissionless blockchains using Veramo and Hyperledger Indy.