Decentralized Identifiers (DIDs) and Verifiable Credentials have gained significant momentum in recent times due to their potential to revolutionize the way we manage and share our personal information online.
In this article, know how to create DIDs and Verifiable Credentials using the Veramo Framework.
What Is Veramo Framework?
Veramo is an open-source JavaScript framework that provides a simple and easy-to-use SDK for creating and managing DIDs and Verifiable Credentials. It is built on top of the Interledger Protocol (ILP) and supports various blockchain platforms, including Ethereum, Bitcoin, and more.
Veramo, collaborate with the W3C and the DIF to ensure compatibility with a multitude of projects and initiatives in the decentralized identity space. Veramo provides flexibility in designing your agent by offering core plugins for various components such as DID Methods, Messaging Protocols, Storage, Key Management, Authentication, and more.
With Veramo, developers can easily implement DIDs and Verifiable Credentials in their applications, enabling them to build more secure and privacy-respecting systems.
Veramo Key Concepts
Veramo is a decentralized identity framework that focuses on various key concepts that are:
1. Verifiable Data
Verifiable data refers to information that can be verified as true and accurate by a trusted party. Additionally, one can obtain this by using Verifiable Credentials, which are signed digital documents that prove claims about individuals.
A Verifiable Credential in Veramo is a digitally signed and encrypted piece of information that serves as proof of an identity attribute or a claim made about an individual. The signature and encryption are used to ensure the integrity and confidentiality of the information, and the fact that a trusted third party verifies the information provides a high level of trust in its accuracy and authenticity.
Here is an example of a Verifiable Credential in Veramo using JSON-LD format. In this example, the verifiable credential attests bachelor’s degree for a subject using a DID of did:example:ebfeb1f712ebc6f1c276e12ec21. The proof is signed by the issuer using the EcdsaSecp256k1Signature2019 signature type.
{ "@context": [ "https://www.w3.org/2018/credentials/v1", "https://www.w3.org/2018/credentials/examples/v1" ], "id": "https://example.com/credentials/3732", "type": [ "VerifiableCredential", "UniversityDegreeCredential" ], "issuer": "did:example:ebfeb1f712ebc6f1c276e12ec21", "issuanceDate": "2010-01-01T19:23:24Z", "credentialSubject": { "id": "did:example:ebfeb1f712ebc6f1c276e12ec21", "degree": { "type": "BachelorDegree", "name": "Bachelor of Science and Arts" } }, "proof": { "type": "EcdsaSecp256k1Signature2019", "created": "2022-07-01T19:23:24Z", "proofPurpose": "assertionMethod", "verificationMethod": "did:example:12q3vfrt8q9we8rqw0efrq0wqe", "signatureValue": "base64(hF+...)" } }
2. Decentralized Identifier
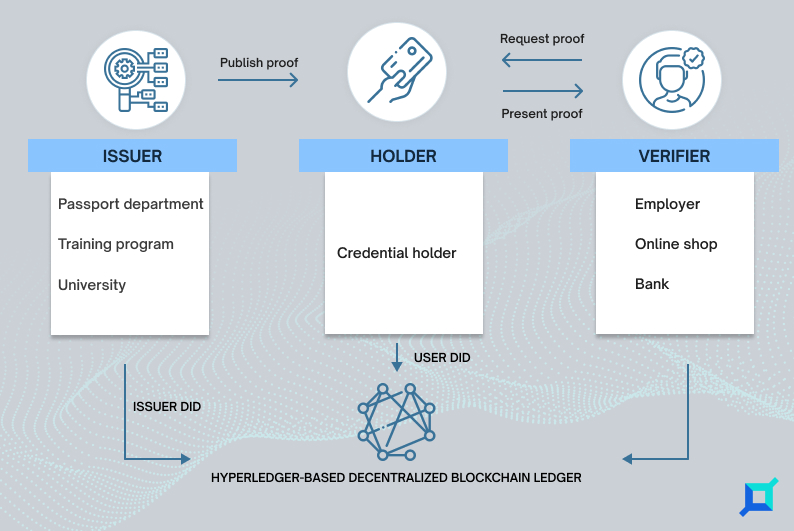
A Decentralized Identifier (DID) is a unique identifier used to refer to a subject in a decentralized system, such as a blockchain or a distributed ledger. In the context of Veramo, a DID can be used to identify a subject of a verifiable credential, such as an individual, an organization, or a device.
DIDs are designed to be self-sovereign, meaning that the subject has control over its own identifier and can manage the associated data without needing a centralized authority. It provides a privacy-preserving and secure way to represent entities with verifiable credentials. Moreover, the DID can be used to ensure that the right data is being shared with the right recipient.
In Veramo, a DID is like a string that starts with the prefix did:, followed by the identifier of the decentralized system where the DID is registered.
Currently, Veramo core supported methods are ether, web, and key.
For example, a DID could look like this: did:ether:ebfeb1f712ebc6f1c276e12ec21.
3. Signing & Key Management
Veramo provides tools and plugins for signing and managing keys associated with DIDs. This includes key management plugins for creating, storing, and retrieving private keys, as well as signing plugins for signing Verifiable Credentials.
4. Plugins
Veramo provides a range of core plugins for DID Methods, Messaging Protocols, Storage, Key Management, Authentication, and more. Developers can use these plugins to design their agents as they see fit.
You can find a complete list of Vermao plugins here.
5. Agents
An agent is a piece of software that acts on behalf of an individual in the decentralized identity ecosystem. Veramo provides tools and plugins to build agents that can create and manage DIDs and Verifiable Credentials.

The Veramo Agent is responsible for performing various tasks, such as:
- Creating identifiers
- Resolving identifiers
- Issuing credentials
- Revoking credentials
- Exchanging credentials
Additionally, the Veramo Agent acts as a central hub, providing a common interface for developers to expand its functionality by using plugins. When instantiated, the Veramo Agent manages both core and custom plugins and orchestrates the core event system.
6. Selective Disclosure Request (SDR)
A Selective Disclosure Request is a feature in the Veramo framework that allows an individual or organization to selectively disclose specific pieces of information from their digital identity. It allows them to control the amount of personal information they share with other parties while maintaining privacy. The Veramo framework uses cryptographic techniques to securely store and share this information, ensuring that only authorized parties can access it.
Steps To Create A DID & Verifiable Credential Using Veramo CLI
Following the below-mentioned steps, you can form a DID and Verifiable Credential using Veramo CLI.
#1 Step: Install Veramo CLI
The first step is to install the Veramo CLI by running the following command in your terminal:
npm i @veramo/cli -g
#2 Step: Create Configuration File
You can create a configuration file in the current folder by running the following:
veramo config create
#3 Step: Create A DID
To create a DID, run the following command:
veramo did create
This command will create a DID and store the keys in a local database.
#4 Step: Resolve A DID
To resolve a DID, use the following command with the identifier of the DID you want to resolve, such as
did:ethr:0xf3abebb0d4f5d7e08c2557772f9ce8692a795ab8.
veramo did resolve your_did_identifier
#5 Step: Create A Verifiable Credential
To create a Verifiable Credential, run the following command:
veramo credential create
Conclusion
In this article, one can learn how to create DIDs and Verifiable Credentials using the Veramo Framework using CLI. The Veramo Framework provides a simple and easy-to-use API for creating and managing DIDs and Verifiable Credentials, making it an excellent choice for developers who are new to the space.
The Veramo framework can be implemented in projects using CLI or SDKs in various languages, including NodeJS, ReactJS, and React Native; you can choose the option that best suits your project requirements.
If you are planning to develop such projects, connect with Infrablok. Our technicians are proficient in Node.js, React.js, and React Native and can assist in developing a DID project using the Veramo framework.