The combination of blockchain and AI represents two crucial and emerging technologies. Blockchain, known for its versatility and ease of implementation, serves as a shared and permanent ledger for future data encryption. On the other hand, AI has surpassed its experimental limitations in performance and enables individuals to analyze data and make informed decisions.
While both technologies have distinct origins, they are intertwined with recent advancements in the tech world. When considering their diverse complexities, it is crucial to recognize that integrating artificial intelligence and blockchain offers numerous advantages.
A survey indicates that blockchain enhances AI’s consistency, comprehensibility, and logical nature. By referring to the ledger, one can delve into the decision-making process of machine learning and understand the reasons behind specific outcomes. The ledger acts as a repository of all data records, aiding decision-making.
So, let’s explore the Futuristic approach of AI and Blockchain…
Bringing Blockchain Technology And Artificial Intelligence Together
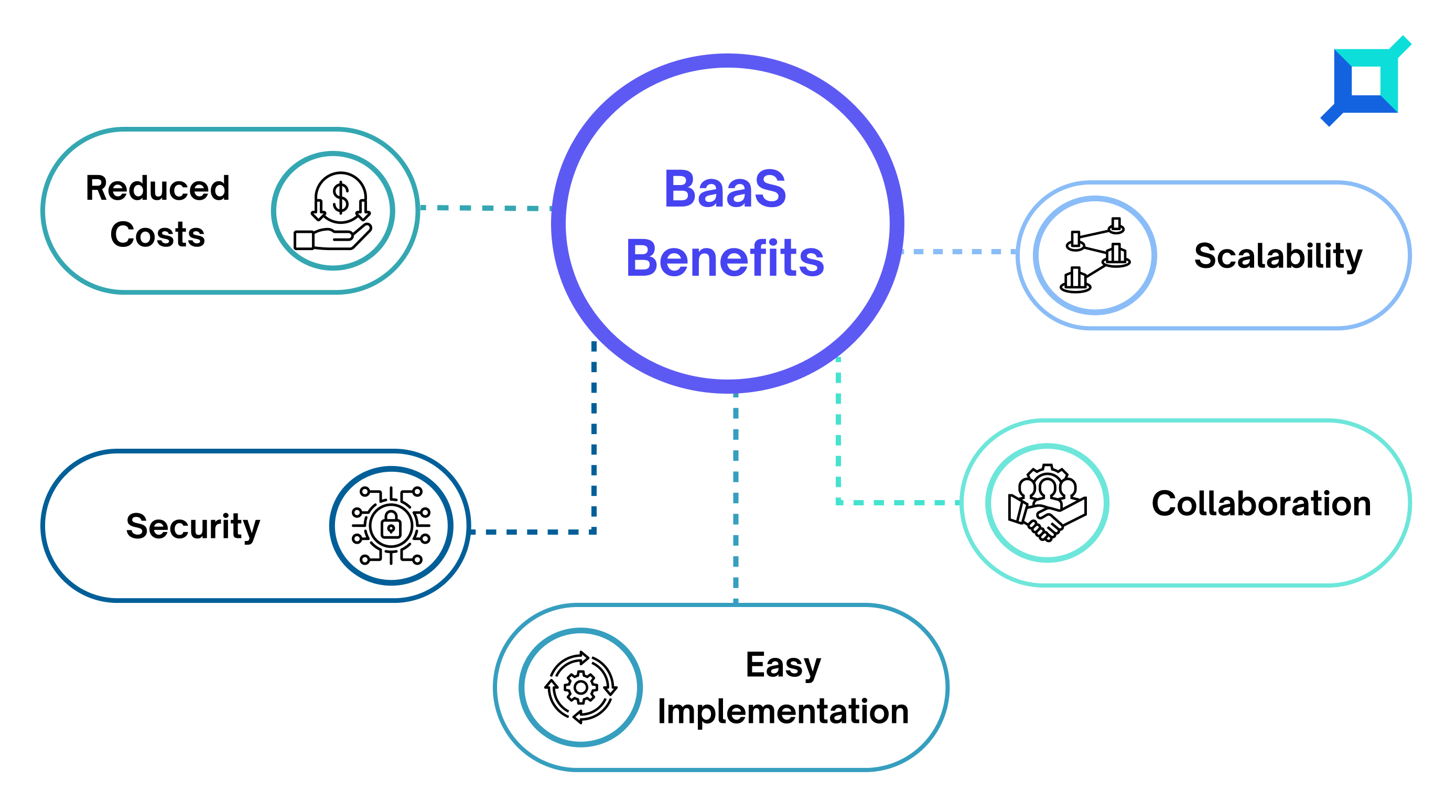
The interlinking of blockchain technology and AI offers several benefits that can enhance various aspects of technological development. Some key advantages include:
1. Enhanced Data Security
Blockchain provides a secure and tamper-resistant platform for storing and managing data. By integrating AI with blockchain, the transparency and immutability of the ledger can be leveraged to ensure the integrity and authenticity of data used in AI models. It helps reduce the risk of data manipulation, fraud, and unauthorized access.
2. Improved Data Quality and Reliability
Blockchain’s distributed nature allows for consensus and data validation across multiple nodes. AI algorithms can leverage this feature to verify the accuracy and reliability of data sources, ensuring high-quality inputs for training models. It helps subside biases, errors, and inconsistencies in the data, leading to more accurate and reliable AI outcomes.
3. Enhanced Trust and Transparency
The transparency provided by blockchain enables greater visibility into AI decision-making processes. Recording all transactions and data manipulations in the blockchain ledger makes it easier to trace and audit the steps leading to a particular AI decision. It promotes trust and transparency, particularly in critical domains like healthcare, finance, and legal systems.
4. Improved Data Privacy and Control
Blockchain technology can empower individuals with control over their personal data. AI systems that utilize blockchain can provide users with greater privacy and control by allowing them to grant selective access to their data. It enables individuals to maintain ownership of their data while still contributing to AI training and research efforts.
5. Efficient Data Exchange and Collaboration
Blockchain facilitates secure and decentralized data sharing among multiple stakeholders. Combined with AI, it enables seamless collaboration and data exchange between different parties, such as researchers, organizations, and individuals. It promotes innovation, accelerates research, and unlocks new possibilities for AI development.
6. Scalability and Decentralization
Blockchain’s distributed architecture allows for scalability and resilience in AI systems. With AI models deployed on blockchain networks, computation and storage can be distributed across multiple nodes, improving efficiency and performance. This decentralized infrastructure also reduces reliance on a single point of failure, increasing the robustness of AI applications.
7. Trustworthy Autonomous Systems
Blockchain’s transparency and immutability can contribute to developing trustworthy autonomous systems. AI algorithms can be deployed on blockchain networks, enabling autonomous decision-making while ensuring transparency and accountability. It is valuable in critical domains such as autonomous vehicles, where trust and reliability are paramount.
The interplay between blockchain and AI can revolutionize various industries and unlock new possibilities for secure, trustworthy, and efficient AI systems.
How Do AI And Blockchain Technology Complement Each Other?
Blockchain technology provides a conventional and costly approach to storing large amounts of data. Storing extensive files on the Bitcoin blockchain, for instance, becomes prohibitively expensive due to the one-megabyte size per block. To address this challenge, data is stored on a decentralized storage medium that connects it to blockchain blocks through hashing or utilizes smart contract code.
The integration of AI and blockchain technologies enable the creation of decentralized AI applications and algorithms that have access to a shared and trusted data platform. This platform serves as a repository for storing knowledge, records, and decisions. It proves particularly beneficial for maintaining reliable records of AI algorithms throughout the learning and decision-making processes, ensuring transparency and accountability at every stage.
The Concept Of A Decentralized AI System
The concept of a decentralized AI system aims to achieve processor independence without the drawbacks of sharing aggregated data. It allows users to process information independently across different computing devices. This approach yields diverse insights, enabling fresh problem-solving approaches that may not be possible in a centralized system.
The potential of a decentralized AI system extends to various domains, such as science, businesses, and meeting public demands. It empowers devices to tackle real-world challenges, engage in trial-and-error learning, and employ reasoning, all while meticulously recording the results. This approach provides a clear and consistent framework for understanding how things operate.
Integrating AI with blockchain technology plays a crucial role in enabling decentralized learning by facilitating secure knowledge sharing and fostering trust in the decision-making process. It opens avenues for substantial autonomous contributions, coordination, and democratic voting in future decision-making. However, the realization of the full impact of decentralized AI requires robust computing power, fast connectivity, and ample storage capabilities.
Security Approaches Of Decentralized AI Platform
Here explore a few of the security approaches of decentralized AI platforms-
Secured Multi-Party Computations (SMPC)
SMPC is a security method used in decentralized AI platforms that allows multiple parties to jointly compute a function on their private data without revealing the underlying data.
Blockchain technology can enhance SMPC by providing a trusted and transparent platform for secure data sharing and computation. SMPC can be executed on the blockchain using smart contracts and cryptographic protocols, ensuring the privacy and integrity of sensitive data used in AI computations.
Generative Adversarial Network (GAN) Cryptography
GAN cryptography is a technique that combines AI and cryptography to protect data privacy in decentralized AI platforms. GANs consist of a generator and a discriminator, which work together competitively to generate synthetic data while preserving the characteristics of the original data.
Blockchain can leverage GAN cryptography to enable secure data sharing and training of AI models on decentralized networks, ensuring confidentiality and preventing unauthorized access to sensitive information.
Homomorphic Encryption
It is a cryptographic technique that allows computations to be performed on encrypted data without decrypting it. In the context of decentralized AI platforms, homomorphic encryption can protect data privacy while allowing for secure and privacy-preserving computations.
Blockchain technology can provide a distributed and transparent infrastructure for executing homomorphic encryption operations, ensuring the confidentiality of data throughout the AI processes performed on decentralized networks.
By incorporating these security methods, such as SMPC, GAN cryptography, and homomorphic encryption, into decentralized AI platforms, the privacy and security of data can be preserved, enabling secure collaboration and computation among multiple parties while leveraging the benefits of blockchain technology.
AI + Blockchain: What’s The Future?
The combination of artificial intelligence and blockchain holds the potential to create an immutable, secure, and decentralized system, resulting in significant advancements in data and information security across diverse industries.
However, the convergence of AI and blockchain technology remains largely unexplored, despite garnering significant attention and ongoing projects dedicated to this groundbreaking fusion. The integration of these two technologies opens up unprecedented possibilities for data utilization.
By harnessing the unique capabilities of AI and blockchain, their collaboration will offer a logical framework for data management and processing. This synergy has the potential to propel data exploitation to unprecedented levels, unlocking new frontiers of innovation and discovery.
Embrace the future of innovation by leveraging the synergies of AI and blockchain to create secure, transparent, and transformative solutions. Take the first step towards unlocking their potential today, and for that, get in touch with Infrablok experts!