Blockchain technology has revolutionized the way businesses store and transfer data, offering a secure and transparent way to manage transactions. However, implementing and managing a blockchain network can be daunting and costly, especially for small and medium-sized businesses (SMBs) that may not have the resources to invest in hardware and software infrastructure. BaaS providers offer a solution to this problem, providing pre-built blockchain networks, tools, and APIs that SMBs can use to build and deploy their blockchain applications quickly and easily.
Benefits Of Preferring Blockchain-as-a-Service (BaaS)
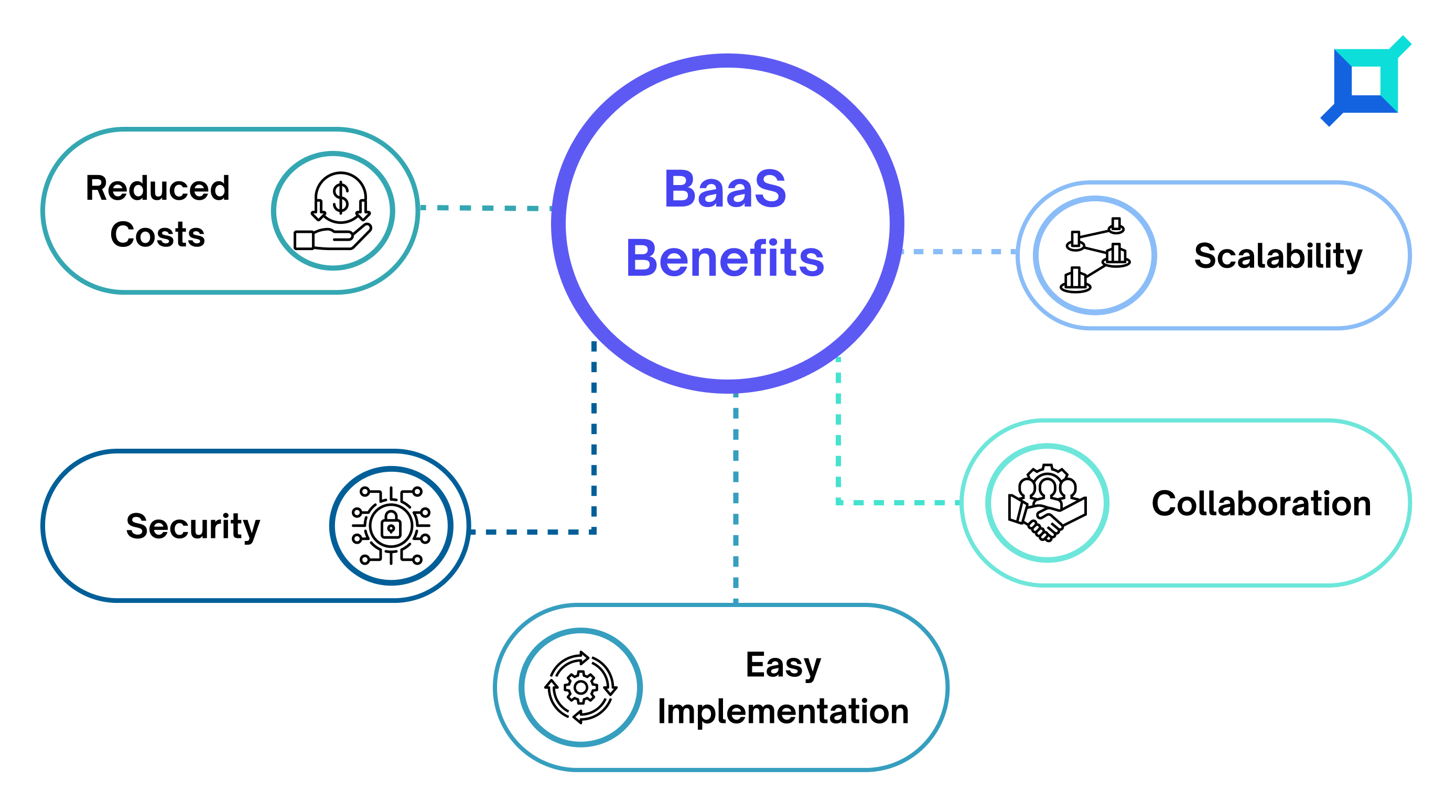
There are many benefits associated with using BaaS, some of which are –
Reduced Costs
One of the primary benefits of BaaS is cost reduction. Blockchain-as-a-Service provider offers subscription-based pricing models, which means SMBs can pay for only the resources they use. This eliminates the need for large upfront investments in hardware and software infrastructure, making blockchain technology more accessible to SMBs. For example, an SMB can use a BaaS provider like IBM Blockchain Platform, which offers a free trial and a pay-as-you-go pricing model, to develop and deploy their blockchain application without incurring high infrastructure costs.
Easy Implementation
Another benefit of BaaS is easy implementation. BaaS providers offer pre-built blockchain networks and tools, which means SMBs can quickly and easily implement their blockchain applications without having to spend time and resources on development and testing.
For example, Microsoft Azure Blockchain Workbench offers a range of pricing options, including a free trial and a pay-as-you-go pricing model, making it an affordable option for SMBs looking to implement a blockchain network without a significant investment in infrastructure.
Scalability
Blockchain-as-a-Service Providers offer scalable infrastructure that can accommodate the changing needs of SMBs as they grow. This means that SMBs can easily add or remove nodes from their network as needed without having to worry about the underlying infrastructure.
For example, Amazon Managed Blockchain offers a simple pricing model based on the number of nodes in the network, which makes it an affordable option for SMBs that require a small number of nodes initially but may need to scale in the future.
Security
BaaS providers offer built-in security measures, such as encryption and authentication, to protect blockchain networks and applications from cyber threats. This means that SMBs can focus on their core operations without having to worry about the security of their blockchain network.
For example, the IBM Blockchain Platform offers a range of tools and APIs to help SMBs build and deploy their blockchain applications securely.
Collaboration
Blockchain-as-a-Service provider provides tools and APIs that enable SMBs to collaborate and share data securely with other businesses and partners. This makes it easier for SMBs to work together and streamline their operations.
For example, Microsoft Azure Blockchain Workbench offers a range of tools and APIs to help SMBs build and deploy their blockchain applications collaboratively.
However, while BaaS Blockchain offers multiple advantages, it also includes a few cons.
Drawbacks Of Blockchain-as-a-Service (BaaS)
The pointers mentioned below will help you understand the BaaS cons.
Limited Control
When using a Blockchain-as-a-Service, SMBs rely on the provider’s infrastructure, which means they have limited control over the underlying technology. This lack of control can be a disadvantage when it comes to customization and flexibility.
Security Concerns
Blockchain technology is still relatively new and complex, and SMBs may not have the necessary expertise to ensure the security of their applications. When using a BaaS provider, SMBs must trust the provider’s security measures and protocols, which can be a risk.
Limited Scalability
Some Blockchain-as-a-Service Providers may not be able to accommodate large-scale blockchain applications or high transaction volumes. This can be a problem for SMBs that need to scale their blockchain applications quickly as their business grows.
Dependency
When using a BaaS provider, SMBs rely on the provider’s availability and uptime. Any downtime or service interruptions on the provider’s side can affect the SMB’s ability to access and use their blockchain applications.
Potential Vendor Lock-In
If an SMB relies too heavily on a BaaS provider, it may become locked into using the provider’s technology and services. This can make it difficult to switch providers or move to a self-hosted solution in the future.
Popular Blockchain-as-a-Service (BaaS) Providers
Some of the popular BaaS providers are –
1. IBM Blockchain Platform
The Platform offers a range of tools and APIs to help SMBs build and deploy their blockchain applications. It also offers a free trial and a pay-as-you-go pricing model, which makes it affordable for businesses of all sizes.
2. Microsoft Azure Blockchain Workbench
It offers a range of pricing options, including a free trial and a pay-as-you-go pricing model, making it an affordable option for SMBs. It also offers a range of tools and APIs to help SMBs build and deploy their blockchain applications.
3. Amazon Managed Blockchain
This platform offers a simple pricing model based on the number of nodes in the network, which makes it an affordable option for SMBs that require a small number of nodes initially but may need to scale in the future. It also offers a range of tools and APIs to help SMBs build and
4. Oracle Blockchain Platform
It is a cloud-based platform that offers a range of tools and APIs to help SMBs build and deploy their blockchain applications. It also offers a flexible pricing model based on usage, which means SMBs can pay for only the resources they use.
5. SAP Cloud Platform Blockchain
This is a Blockchain BaaS platform that enables SMBs to build and deploy blockchain applications using pre-built templates and tools. It also offers a flexible pricing model based on usage, which means SMBs can pay for only the resources they use.
6. Alibaba Cloud BaaS
The blockchain platform enables SMBs to build and deploy blockchain applications using pre-built templates and tools. It also offers a range of pricing options, including a free trial and a pay-as-you-go pricing model.
7. Binance Smart Chain
It is a decentralized blockchain platform that enables SMBs to build and deploy blockchain applications using pre-built tools and APIs. It offers affordable transaction fees and fast transaction times, making it an attractive option for SMBs looking to build blockchain applications on a budget.
Wrapping Up
Blockchain-as-a-Service is a cost-effective way for businesses to implement and manage blockchain-based applications. By leveraging the infrastructure and tools provided by Blockchain-as-a-Service providers, businesses can focus on developing and deploying their applications rather than managing the underlying infrastructure, but before selecting a provider, they must carefully evaluate the pros and cons of choosing a BaaS provider before making a decision.
It’s important to choose a provider that offers the right balance of affordability, security, scalability, and control to meet the SMB’s specific needs. We at Infrablok can help you choose the best BaaS solution for all your business needs. Contact us if you wish to know more about it!