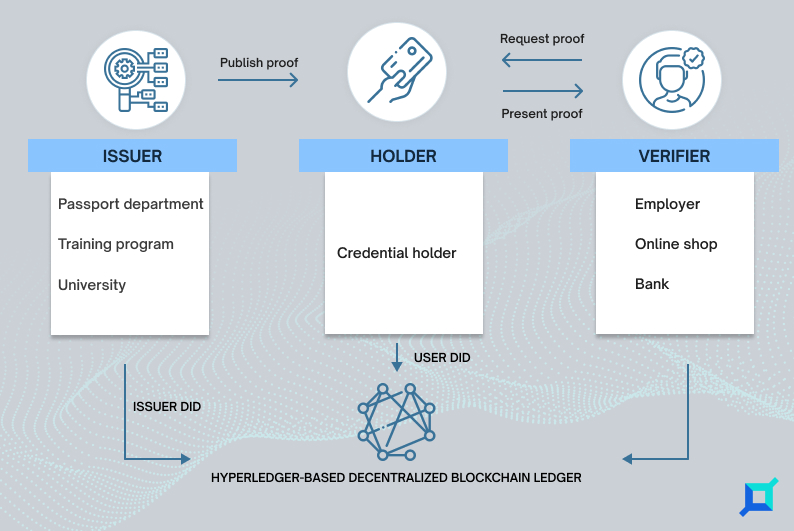
Hyperledger Indy is an open-source framework based on distributed ledger technology for providing self-sovereign identity. It is one of the Hyperledger projects hosted by The Linux Foundation.
Indy provides a framework for creating and managing digital identities that are verifiable, private, and portable. Allowing individuals and organizations to create, manage, and store their own digital identities and provide tools for verifying the authenticity of these identities.
It is designed to be a foundation for developing various identity-related applications, such as digital identity verification, secure sharing of personal information, and digital signing. It is also suitable for use cases such as providing secure access to online services, creating digital identities for IoT devices, and enabling secure communication between organizations.
Indy is built using a modular architecture, which allows developers to add new features and functionality and customize the platform to meet their specific needs.
In summary, Hyperledger Indy offers a distributed ledger technology that allows individuals and organizations to create, manage, and store their own digital identities securely and independently. Its flexible and modular architecture allows developers to add new features, customize them to their specific needs, and build various identity-related applications.
Hyperledger Indy’s Key Features
Hyperledger Indy has several key features that make it well-suited for use cases related to digital identity management:
1. Self-Sovereign Identity
Hyperledger Indy provides individuals and organizations with the ability to create, manage and control their own digital identities without the need for a centralized authority.
2. Decentralized & Distributed
Indy uses a decentralized and distributed ledger technology, which ensures that digital identities are tamper-proof and transparently managed.
3. Verifiable & Private
Indy allows for the creation of digital identities that are verifiable, private, and portable. It uses digital signatures to verify the authenticity of identities and encrypts personal information to protect privacy.
4. Interoperable
It is designed to be interoperable with other identity systems and can be integrated with other technologies, such as biometrics and blockchain.
5. Modular Architecture
Indy’s modular architecture allows developers to add new features and functionality to the platform and customize it to meet their specific needs.
6. Scalable
It can handle a high volume of transactions and many digital identities, making it suitable for large-scale use cases such as providing digital identities for IoT devices.
7. Compliance
Hyperledger Indy’s design allows for compliance with various regulations and standards, such as GDPR, HIPAA, and others.
8. Identity Verification
Indy provides a framework for creating and managing digital identities that are verifiable, private, and portable. It allows individuals and organizations to create, manage and store their own digital identities and provides tools for verifying the authenticity of these identities.
9. Secure Access To Online Services
Hyperledger Indy enables secure access to online services with the use of digital identities.
Hyperledger Indy Benefits
Here view a few crucial user-centric features of Hyper Hyperledger Indy:

The Hyperledger Indy Projects
It is composed of several projects that work together to provide a platform for self-sovereign identity management. These projects include:
- Indy Node: The core component of Hyperledger Indy, responsible for maintaining the distributed ledger and providing a RESTful API for interacting with the ledger.
- Indy SDK: A software development kit that provides libraries and tools for building applications that interact with Hyperledger Indy.
- Indy CLI: A command-line interface for interacting with the Hyperledger Indy platform.
- Indy Plenum: A Byzantine Fault Tolerant (BFT) consensus algorithm for the Hyperledger Indy platform.
- Indy Agent: A software agent that can act on behalf of a digital identity and perform actions such as creating and managing digital credentials.
- Indy Wallet: A client-side library for managing digital identities and digital credentials in a secure and user-friendly way.
- Indy Credx: A library for creating and managing digital credentials that can be used to prove attributes of a digital identity.
- Indy Anoncreds: A library for creating and managing anonymous credentials that can be used to prove attributes of a digital identity without revealing the identity itself.
- Indy Ledger: A library for creating and managing a distributed ledger, which is the backbone of the Hyperledger Indy platform.
- Indy Config: A library for configuring and customizing the Hyperledger Indy platform for different use cases and deployment scenarios.
Together, these projects provide the necessary tools and functionality for creating, managing, and verifying digital identities on a decentralized and distributed ledger, as well as building various identity-related applications.
8 Simple Steps To Create DID Using Hyperledger Indy CLI
Here is a step-by-step guide to creating a Decentralized Identifier (DID) using the Hyperledger Indy CLI:
Step 1
Instal a version of libindy that’s built, installed, and callable in the system path. For building and installing libindy follow the instruction here.
Step 2
Run the Indy pool on your system. To run an Indy pool, follow the instruction in a given document.
Step 3
Start the CLI by running the command “indy-cli” in the terminal.
Step 4
Create a new wallet by running the command “wallet create” and by providing a name and passphrase for the wallet while entering the command.
wallet create your_wallet_name -key

Here are the options available when creating a new wallet with the Hyperledger Indy CLI:
name - Identifier of the wallet key - (leave empty for deferred input) Key or passphrase used for wallet key derivation. Look at the key_derivation_method param for information about supported key derivation methods. key_derivation_method - (optional) Algorithm to use for wallet key derivation. One of: argon2m - derive secured wallet key (used by default) argon2i - derive secured wallet key (less secure but faster) raw - raw wallet key provided (skip derivation) storage_type - (optional) Type of the wallet storage. storage_config - (optional) The list of key:value pairs defined by storage type. storage_credentials - (optional) The list of key:value pairs defined by storage type.
Examples:
wallet create your_wallet_name key
wallet create your_wallet_name key storage_type=default
wallet create your_wallet_name key storage_type=default storage_config={"key1":"value1","key2":"value2"}
Step 5
Open the wallet by running the command “wallet open” and by providing the wallet name and passphrase.
wallet open your_wallet_name key

Step 6
Create a new DID (Decentralized Identifier) by running the command “did new” and providing a seed (a string of random characters) for the DID. The seed is used to generate the private key for the DID.
didnew [did=<did-value>] [seed[=<seed-value>]] [method=<method-value>] [metadata=<metadata-value>]

Here are the options available when creating a new DID with the Hyperledger Indy CLI:
- did – (optional) Known DID for new wallet instance
- seed – (oponal) (leave empty for deferred input) Seed for creating DID key-pair (UTF-8, base64 or hex)
- method – (optional) Method name to create fully qualified DID
- metadata – (otiptional) DID metadata
Examples:
did new did=VsKV7grR1BUE29mG2Fm2kX did new did=VsKV7grR1BUE29mG2Fm2kX method=indy did new did=VsKV7grR1BUE29mG2Fm2kX seed=00000000000000000000000000000My1 did new seed=00000000000000000000000000000My1 metadata=did_metadata
Step 7
Verify that the DID was created and stored by running the command “did list” which should show the newly created DID in the list of identities stored in the wallet.

Step 8
Use the DID to sign and verify messages or to encrypt and decrypt data by using the corresponding commands.
Hyperledger Indy Use Cases

Wrapping Up
In conclusion, creating a Hyperledger Indy DID use the command-line interface (CLI) is a straightforward process that involves installing the Indy CLI, creating a new wallet, generating a new DID, and storing the DID in the wallet. By following the steps outlined in this blog post, developers can quickly and easily create a new digital identity using Hyperledger Indy. This is just the beginning of what Hyperledger Indy can do.
The possibilities are endless as it can be integrated with other technologies (NodeJS, .NET, and Python) to create robust and secure decentralized applications. Hyperledger Indy is a powerful tool for building decentralized identity systems and is well-suited for a wide range of use cases, from enterprise and government applications to personal identity management; if you are planning to develop such projects, connect with Infrablok. It will help you get experts who can help you design apps from scratch.